In the early days of macOS Mojave in 2018, Apple hadn’t offered users a way to automatically switch to dark and light mode at different times of the day. As usual, there were third-party developers eager to pick up the slack. One of the more well-regarded night mode apps to fix this issue was NightOwl, first released in the middle of 2018, a small app with a simple utility that could run in the background during day-to-day use.
With more official macOS features added in 2021 that enabled the “Night Shift” dark mode, the NightOwl app was left forlorn and forgotten on many older Macs. Few of those supposed tens of thousands of users likely noticed when the app they ran in the background of their older Macs was bought by another company, nor when earlier this year that company silently updated the dark mode app so that it hijacked their machines in order to send their IP data through a server network of affected computers, AKA a botnet.
After some users noted issues with the app after a June update, web developer Taylor Robinson discovered the problem ran deep, as the program redirected users’ computers’ connections without any notification. The real dark mode turned out to be the transformation of a respectable Mac app into a playground for data harvesters.
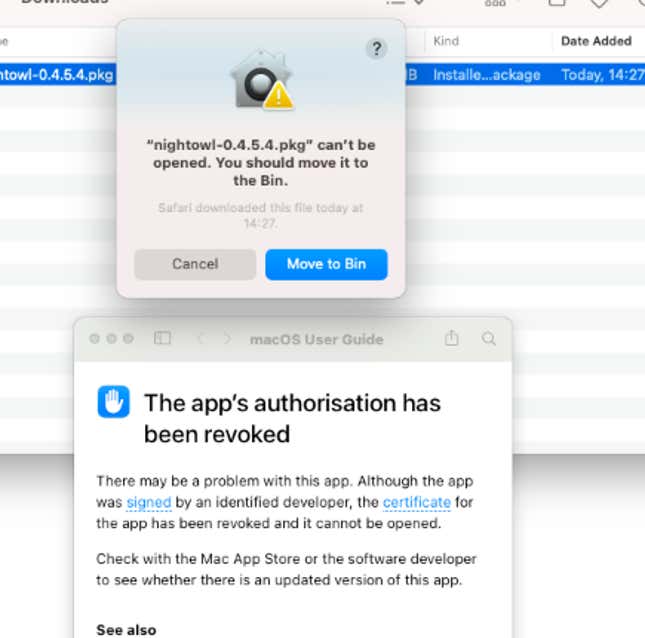
In an email with Gizmodo, Robinson broke down their own investigation into the app. They found that NightOwl installs a launcher that turns the users’ computer into a kind of botnet agent for data that’s sold to third parties. The updated 0.4.5.4 version of NightOwl, released June 13, runs a local HTTP proxy without users’ direct knowledge or consent, they said. The only hint NightOwl gives to users that something’s afoot is a consent notice after they hit the download button, saying the app uses Google Analytics for anonymized tracking and bugs. The botnet settings cannot be disabled through the app, and in order to remove the modifications made to a Mac, users need to run several commands in the Mac Terminal app to excise the vestiges of the code from their system, per Robinson.
It’s currently unclear how many users were affected by the seemingly malicious code, especially as NightOwl has since become unavailable on both the website and app store. The NightOwl site claims the app was downloaded more than 141,000 times, and that there were more than 27,000 active users on the app. Even if the app lost most of its users after Apple installed new Dark Mode software, there were potentially thousands of users running NightOwl on their old Macs.
Days after Robinson released their report calling the app subversive malware, NightOwl included a comment on its site reading: “Our app does not contain any form of malware. The concerns raised are based on a mistaken identification, and we are actively working with all major antivirus companies to rectify this situation promptly.”
It’s unclear what the company means by “all major antivirus companies” and how it plans to change its app. Robinson noted the app seems purpose built to remain anonymous, as the botnet connection forcibly runs on the Mac’s main user account and launches when users boot up their device. The web developer first noticed the odd traffic when they were analyzing their network traffic for an unrelated matter. All that traffic was coming from their computer to sites they had never heard of before. Sure, other obvious botnet schemes might try to game ad revenue, but even though selling user data is common practice, most apps don’t need to resort to forcibly installing software that boots every time a opens their device.
But it is clear the company had plans to include this botnet behavior, as the owners put a note on NightOwl’s Terms of Use page before releasing the latest update, which included the malware-like activity. Gizmodo reached out to the owners of the NightOwl app multiple times, but we did not receive a response. However, the group that currently owns the app did respond to HowtoGeek, stating:
“We have partnered with a respected residential proxy service to monetize NightOwl. We added their SDK to the backend of the app that allows our partner’s users to send some requests through NightOwl user’s IP address. It’s important to note that we solely collect users’ IP addresses. No other user data is collected. We have disclosed this in our terms and conditions.
Given some users’ high level of concern, we are working to give users an option to opt out of this. If we are able to re-release the app we will either completely remove this SDK or give an easy option for disabling. We apologize for the inconvenience and concern created.”
Robinson told Gizmodo there’s nothing to show that the company collected anything more than IPs through the botnet. However, the app owners were still trying to cover their tracks “as much as possible,” Robinson said. The app owner named the background botnet service “AutoUpdate,” and the redirecting software launched whenever a computer with NightOwl booted up, according to Robinson.
The app did not notify users it had auto-updated to turn their computers into a wellspring for their own data, Robinson said. The only hint any changes were made to the five-year-old app was language added to NightOwl’s terms of use page back in June. The TOS says that the app forces users’ computers to become a “gateway” to share their internet traffic with third parties. The TOS page further says the app modifies their device’s network settings, and the device “acts as a gateway for NightOwl app’s Clients, including companies that specialize in web and market research, SEO, brand protection, content delivery, cybersecurity, etc.”
The app’s signing certificate, necessary to make it available in the Apple App Store, has been revoked, and users are no longer able to access it. We reached out to Apple to see if it was the company or the app developers themselves who revoked it, but we did not hear back.
If you have the NightOwl app installed on your Mac, you should get rid of it immediately. Robinson’s blog details the Terminal commands needed to excise the app from your device.
NightOwl was bought out, then turned into a Trojan Horse
The original NightOwl app was created by German developer Benjamin Kramser back in 2018. As he described on his own site, Kramser made NightOwl because there were “usability issues” with the dark mode on macOS Mojave. After the release, he enjoyed several positive articles and YouTube videos praising his app.
The 0.3.0 version of NightOwl released late in 2020 was signed by Kramser as the main developer. Two years later, a new version of 0.3.0 hit the App Store. According to data shared by Robinson, this new version of the app was instead signed by another individual, Munir Ahmed. That version of the app added a new backend SDK but still lacked the botnet Robinson later noted.
In November 2022, a company publicly registered as TPE.FYI LLC acquired the app, according to a message by Kramser posted to his site. The company went publicly by Keeping Tempo. According to existing records, it was established by several ex-sales software devs with the noble goal of crafting an app to disrupt the ticket price monopoly companies like Ticketmaster has on the music industry. Keeping Tempo was headed by CEO Jarod Stirling and was headquartered in Austin, Texas. However, the latest information on the LLC was that it went inactive earlier this year after failing to file its franchise tax return, according to publicly available data on OpenCorporates.
It’s unclear if Keeping Tempo is fully defunct and what enterprise currently operates under that name. Users found the name “TPE-FYI, LLC” was included in the files as part of the June NightOwl update which established the botnet documented by Robinson. Despite the new owners, the Nightowl site still includes quotes from Kramser about developing the app as well as links to articles from 2018 that originally extolled NightOwl’s features.
One NightOwl user asked Kramser about the botnet activities on his Twitter before the app was removed. The developer said he had no knowledge about the changes to the app, and added he planned to ask the owning company about NightOwl’s activities. Gizmodo contacted Kramser through Twitter DM, and the developer reiterated the same statement he published to his website. He claimed on his website that he sold the company last year “due to time constraints” on keeping the app operational. He did not answer Gizmodo’s questions about who currently owns the NightOwl app.
“This decision was made with the understanding that new (Pro) features and a subscription model would be introduced,” Kramser said. “Unfortunately, ‘TPE.FYI LLC’ has opted to monetize the app by integrating a third-party SDK. This decision is not affiliated with me in any way, and I do not endorse it in any form.”
Even if Kramser truly had no knowledge of the buying company’s ill-intent, Robinson said that there’s still good reason to be skeptical about the app buyout.
“You must know that when a shady company is offering to buy your application, they’re not going to use the entirely user-positive ways of recouping their investment, but that doesn’t make him a villain either, as some people on social media are saying,” the internet sleuth said.
How Do Old Apps Get Corrupted?
This is not the first time reliable-seeming apps have worked as Trojan Horses after already being installed on users’ computers. Go back to any year and you’ll find legit-seeming apps abusing consumers’ trust. Back in 2013, the popular Brightest Flashlight App was sued by the Federal Trade Commission after allegedly transmitting users’ location data and device info to third parties. The developer eventually settled with the FTC for an undisclosed amount.
Software developers discovered the Stylish browser extension started recording all of its users’ website visits after the app was bought by SimilarWeb in 2017. Another extension, The Great Suspender, was flagged as malware after it was sold to an unknown group back in 2020. All these apps had millions of users before anyone recognized the signs of intrusion. In these cases, the new app owners’ shady efforts were all to support a more-intrusive version of harvesting data, which can be sold to third parties for an effort-free, morals-free payday.
App development is both hard and expensive, and for individual creators, it’s tempting to sell when the chance comes along. Robinson said they’ve been there before, having developed an app for free and experienced how costly it is.
“Why put hours into something you’re not getting something out of when you can sell it to someone who will take that load off your hands, right?” Robinson said. “I’m not sure of the financial situation of some of these developers, but if you’re struggling to pay rent every month, and you’re being offered five figures a month, you’re going to take the money and sacrifice a little bit of your morals.”