The crypto market’s volatility, the slow adaptation of regulations, and the frequency of numerous high-profile hacks, scams, and frauds are no secret.
According to Chainalysis, crypto-related crimes reached a staggering $20.6 billion in blockchain transactions in 2022. These figures will most likely rise this year.
However, investors with a deeper understanding of secure crypto practices have an extra edge. Perhaps you’ve come across phrases like ‘be your own bank‘ and ‘not your keys, not your crypto,’ suggesting that taking control of your digital assets is safer, but are you really safe? Let’s dive in!
Understanding the Investor’s Responsibility
Many individuals have been apprehensive about cryptocurrency due to the inherent security risks, primarily because the onus of safeguarding the investment rests solely on the investor. Unlike traditional FDIC-insured bank accounts, cryptocurrencies lack significant government regulations, leaving investors with limited legal recourse in case of loss or theft.
Protecting your cryptocurrency investment is crucial as retrieving lost or stolen funds is extremely challenging, and the responsibility lies with you.
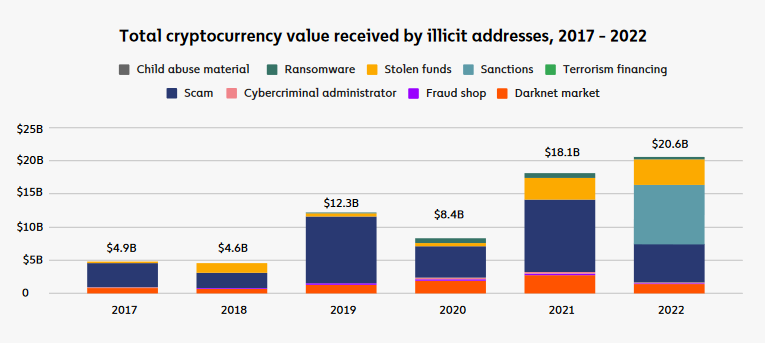
Source: Chainalysis
Hackers employ two primary methods to steal cryptocurrencies: directly accessing them or deceiving users into willingly handing over their digital assets.
What Are The Most Common Crypto Scams?
There are various types of scams that you are likely to encounter. It is crucial to familiarize yourself with these scams to avoid becoming a victim and potentially losing your valuable assets.
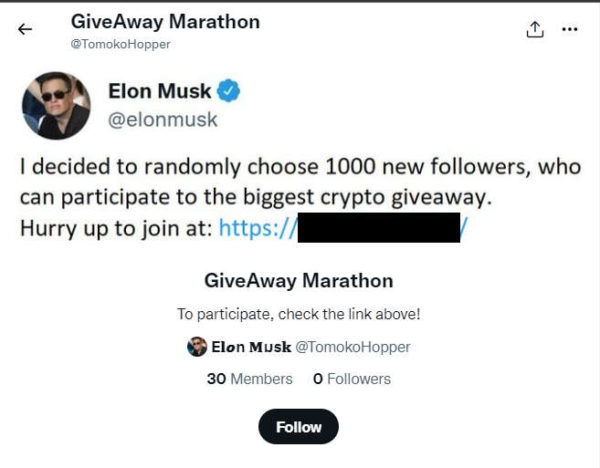
1. Fake Crypto Giveaways: These scams often surface on social media platforms, enticing users to deposit their crypto to a specified address with the promise of receiving double or even more in return. So, crypto scammers use the identities of celebrities or business icons to promote their fraudulent schemes. Recognizing fake crypto giveaway scams becomes easier once you know what to look for. Remember, genuine giveaways from reputable sources never ask you to send money first. Here is an example:
2. Trading Bot Scams: These fraudulent platforms promise users incredibly high monthly returns through trading bots. However, these websites typically operate as Ponzi schemes, using new investments to pay existing participants. When the scammers amass enough funds, they disappear, leaving investors empty-handed. A notorious example of this was Bitconnect, which eventually collapsed, stealing over $250 million.
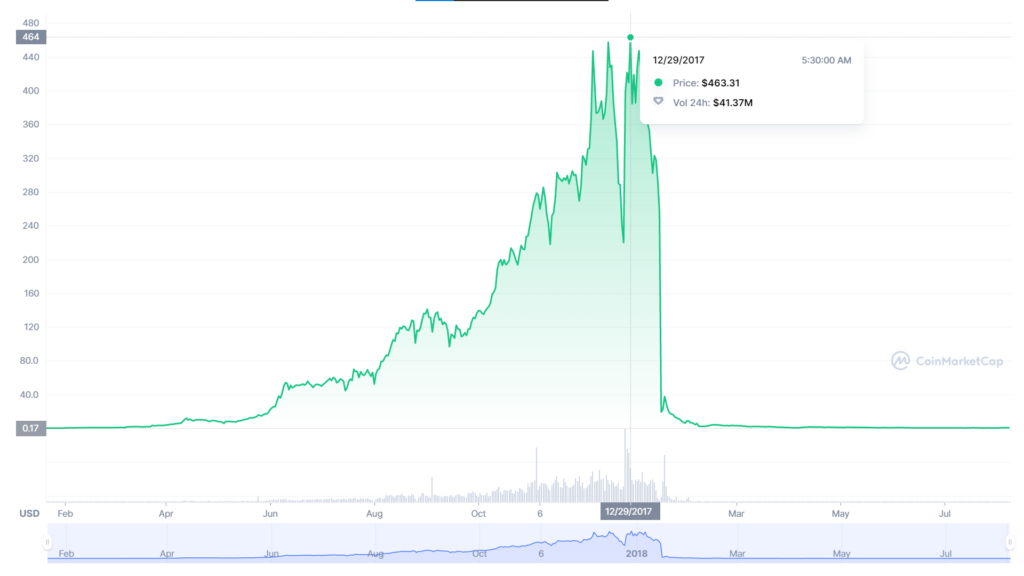
Source: CoinMarketCap
3. Phishing Emails: Phishing scams have become increasingly sophisticated, making it harder to detect their deceitful nature. Malicious agents craft seemingly authentic emails from legitimate companies, luring recipients to click on malicious links that can infect their devices with malware or lead them to imposter websites. These tactics grant scammers access to sensitive information, including web3 credentials.
Phishing scams are particularly prevalent in emails.
They are used as a way to collect your sensitive information by impersonating someone you trust.
Use the blog below to learn how to stay safe from them. https://t.co/UtKBvR52lX
— Binance (@binance) July 4, 2023
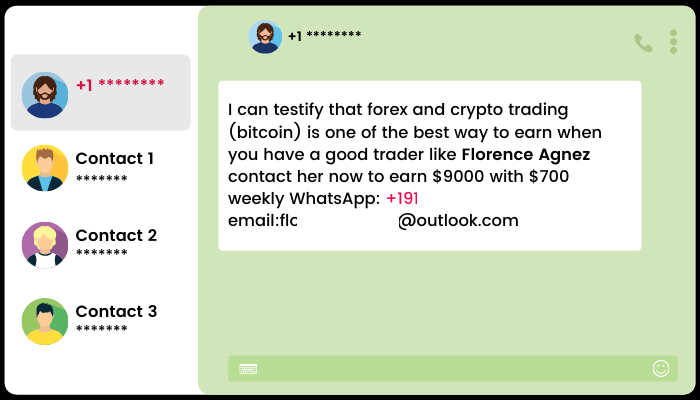
4. Investment Schemes: Scammers pose as experienced “investment managers” and approach potential victims, boasting about their successful cryptocurrency investments and promising significant profits. To begin the investment process, scammers request upfront fees. However, instead of delivering on their promises, they merely steal the fees and may even gather personal identification information for further exploitation.
5. Rug Pull Scams: In rug pull scams, investment scammers hype up new projects, NFTs, or coins to attract funding from unsuspecting investors. They vanish once they accumulate the money, leaving investors with worthless assets. The bad actors often design these scams to prevent investors from selling their cryptocurrency, trapping them in a valueless investment. OneCoin rug pull is an infamous example.
How Can I Be Safe From These Scams?
It is undeniable that transacting online carries inherent risks, and similar habits that ensure online safety can also protect your cryptocurrency. Securing your crypto wallet necessitates adopting practices akin to those used for securing online banking. Nevertheless, there are some additional measures you can implement to safeguard your cryptocurrency investment effectively.
1. Cold Wallets Are The Key!
When investing in digital currencies or NFTs, many investors purchase these assets through exchanges and store them on the platform. While digital exchanges implement safety measures to prevent theft, they are not immune to hacks or potential collapses, as seen with examples like Mt. Gox, FTX, Celsius, Voyager, and others.
For crypto holders who prioritize self-custody, Web3 wallets are the safest option. It aligns with the fundamental principle of decentralization. There are two primary types of cryptocurrency wallets: Cold and Hot wallets. The more secure choice is “cold storage” or “hardware wallet” devices. Cold wallets resemble USB drives and function as physical stores for tokens or coins. Their offline nature ensures that bad actors cannot hack it online.
14/ Thanks for reading, and stay safe out there
Let me know what you think of this thread, if you found this helpful, or if there are other topics I can help you with!
You can find the full article below
https://t.co/jjNAmuTBnj
— Casual Shrimp | Matthew (@acasualshrimp) August 31, 2023
Each hardware wallet has a private key, similar to a password, which decrypts the wallet and grants access to the stored coins or tokens. While hardware wallets effectively guard against digital thieves, losing the password key can permanently lose wallet contents.
Ledger is a standout example of a reputable hardware wallet. It is renowned for its robust security measures that protect crypto currency’s private keys under multiple layers of security within a sophisticated USB stick. Other trustworthy cold wallet alternatives besides Trezor and Ledger Nano include KeepKey, CoolWallet Pro, and SecuX V20.
Undoubtedly, choosing a reliable hardware wallet is crucial for ensuring the safety of your cryptocurrency holdings and embracing the concept of self-custody in the decentralized crypto space.
2. Use Multisig Wallets
In certain situations, having multiple levels of approval for crypto transactions is advantageous. Multi-signature wallets, commonly called “multisig wallets,” exemplify this concept. These wallets require at least two private keys to sign a transaction.
Picture a secure locker equipped with two locks, each with its corresponding key held by two parties. You can only open the locker when both parties provide their keys, ensuring that neither party can access the contents without the other’s authorization.
Why are multisigs becoming the default web3 security paradigm?
On this week's episode of @ValidatedPod, @SimkinStepan from @SquadsProtocol dives into using multiple signature wallets to improve security, building a multisig on Solana, & more.
Watch: https://t.co/hiN5V6aBu8 pic.twitter.com/ZlAidZIjco
— Solana (@solana) September 5, 2023
Using multiple signatures to authorize a transaction significantly enhances the security of your crypto holdings. Potential thieves would need access to all your private keys to gain control over your funds, making it considerably more challenging for them to steal your assets. The additional layer of protection provided by multisig wallets adds an extra safeguard to your crypto assets.
3. Use Multiple Wallets
If you have two dozen eggs, which option would be riskier? Is it putting all 24 eggs in a single basket or dividing them equally into two baskets? If the basket holding all the eggs were to fall, every single egg would break. However, if you had two baskets and only one fell, only half of the eggs would be lost. So, diversification is key. Never place all your eggs in one basket.
The same principle applies to crypto trading. In the DeFi world, as a user interacts with multiple protocols and dApps, the risks of exploits, hacks, or phishing attempts increase.
Instead of holding all your NFTs and cryptocurrencies in one wallet, dividing them into at least two separate wallets is advisable. One wallet, a “hot” wallet, can be used for day-to-day transactions, while the other, a “cold” wallet, can be reserved for long-term HODLing.
11 Ways I Protect My Digital Assets:
-Use a Hardware Wallet
-Multiple Wallets
-Faraday bag
-Store in a safe
-Strong password
-Metal Card for seed phrases
-2FA
-Keep software up-to-date
-Never use public wi-fi
-Don't click weird links
-Limit personal info shared#XRP #Crypto— Vandell | Black Swan Capitalist (@vandell33) March 26, 2023
On a side note, platforms like Metamask and Ledger can create numerous wallets under the same seed. However, it’s essential to be cautious since if someone gains access to your seed; they could access all your wallets.
4. Keep Your Seed Phrase Safe
A seed phrase comprises 12 to 24 random words generated by wallet services like MetaMask. When signing up, it is crucial to enter this seed phrase in the exact sequence provided.
So, beware of scams where individuals impersonate representatives of wallet companies and ask for your seed phrase. Legitimate companies will never request such sensitive information. Therefore, it is critical to NEVER EVER SHARE YOUR SEED PHRASE!
Stamp your seed phrase into titanium
Backup your hardware wallet
Keep your #Bitcoin safe pic.twitter.com/xT26PNUP8u
— Stamp Seed
(@Stamp_Seed) September 4, 2023
Unfortunately, there is no “forgot your password” option to fall back on. If you lose your seed phrase, you will lose access to your wallet entirely, without any exceptions. To ensure its safety, keep the seed phrase offline and secure. Write it on paper and store it where you typically keep your valuable belongings. By doing so, you can protect your access to the wallet and safeguard your digital assets.
5. Use MFA
MFA (Multi-Factor Authentication) establishes a layered defense for your account by employing independent credentials, including a password, security token, or biometrics. The concept behind MFA is “knowing and having”: you know your password, and you possess a token, push notification, biometrics, etc.
When configuring MFA, you typically can choose between SMS or a two-factor authentication (2FA) app push notification. Generally, 2FA is preferable because if an attacker gains control of your SIM card, they can intercept the SMS notification and potentially compromise your account.
Fight against crypto-related digital attacks! Stay ahead with these savvy tips:
Use strong passwords & 2FA for your crypto wallets
Keep your devices updated
Be cautious of phishing attempts
Stay up to date about the latest security threats#SecureYourCrypto
— Uphold (@UpholdInc) September 4, 2023
One method frequently employed by attackers is SIM swaps, which allow them to gain unauthorized access to accounts. If your phone gets stolen, immediately contacting your mobile operator to cancel your old SIM card is crucial.
6. Secure Your Devices And Yourself!
Adhering to general security measures is fundamental for maintaining a safe online environment, especially in Web3. Here are some critical aspects to consider:
- Keep Strong and Unique Passwords: A study reveals that 75% of millennials in the US employ the same password across multiple devices. Given the prevailing risks in today’s environment, it is reasonable to assume that bad actors may eventually breach your passwords. Therefore, the key to protecting your password is to create a complex and unique one, store it securely, and change it regularly. Also, avoid using the same password across multiple devices and platforms. Avoid using personal information in your passwords, and refrain from reusing existing passwords. Moreover, use a password manager to help securely store and generate strong passwords.
- Use a Secure Internet Connection: Avoid accessing your online cryptocurrency exchange or accounts through public WiFi networks. Utilize a VPN whenever possible to hide your IP address and location, ensuring data privacy and protection against eavesdropping and tracking. Setting up a strong and unique password for your WiFi network is equally important to prevent unauthorized access.
- Protect Your Devices: Secure your devices by implementing system updates, installing robust anti-virus and firewall protections, and avoiding pirated software. This layer of defense is crucial for digital investors. Furthermore, separate your Web3 usage from personal and work devices/accounts, and consider creating a dedicated email for your crypto wallet. Avoid accessing your crypto wallet on public or work computers, and consider using a separate device like a dedicated laptop or smartphone for crypto trading. Utilizing encrypted emails also enhances your security.
The correct answer is: All Of The Above!
Distinguishing between an opportunity and scam in Web3 can be challenging.
Looking for tips and best practices to help keep your #crypto secure?
What Is A Rug Pull: https://t.co/0kEXd0lcCI
How To Spot Scams: https://t.co/aSD8e4CN0a pic.twitter.com/YIzelwUCmJ
— Binance.US
(@BinanceUS) September 1, 2023
7. Be Aware of Phishing Scams
Phishing scams pose a significant threat to users’ cryptocurrency holdings. It is crucial to exercise caution and follow these guidelines:
- Be cautious with unfamiliar emails and ads: Avoid opening emails or clicking on suspicious or unexpected ads, especially if they pertain to cryptocurrency. Fraudsters often use phishing tactics to trick users into revealing sensitive information.
- Stay vigilant while accessing crypto-related websites: Ensure you visit the correct URLs when accessing cryptocurrency-related platforms. Avoid clicking on links sent via emails or messages, as these may lead to fake websites that steal login credentials or private keys.
- Exercise caution with search engine sponsored links: Sponsored links on search engines may sometimes lead to malicious websites. Avoid clicking on Google-sponsored pages and opt for reputable sources when searching for crypto-related information.
8. Use Crypto-Safe Practices
DYOR, an abbreviation for “Do Your Own Research,” holds paramount importance as a guiding principle for ensuring safety within web3. There are three crucial aspects to pay attention to:
- Double-Check Everything: Always verify the authenticity of information, including social media accounts, websites, smart contract addresses, etc. Scrutinize each detail to avoid falling victim to scams or fraudulent activities.
- Beware of Unsolicited DMs: Exercise caution when receiving unsolicited DMs on various social platforms. Be skeptical of offers, promotions, or requests coming from unknown sources.
- Beware of Random Airdrops: Stay vigilant when encountering unexpected NFT or token airdrops. Be cautious of disguised free offerings that attempt to compromise your security.
Besides, using dApps like Revoke Cash can add an extra layer of security to your crypto wallet and the Web3 Dapp ecosystem. These dApps offer vaults with approval steps, ensuring that automated allowances are granted only after explicit permission from the user.
Additionally, verifying whether the crypto project you are interacting with has undergone a thorough audit by a reputable third-party auditor like CertiK is advisable.
Furthermore, double-check the wallet address you are sending funds, as certain viruses can modify addresses to redirect funds. Conduct test transactions before sending significant amounts to ensure accuracy and security. For receiving crypto, consider using a domain like ENS (Ethereum Name Service) to simplify the process and use a recognizable name like “abhay.eth” instead of a lengthy 32-character address.
A Brazilian YouTuber lost all his money live on air by accidentally opening a notepad containing his private key.
Safeguarding your crypto assets is paramount. When it comes to self-custody digital wallets, remember:
Keep your private keys offline and secure.
Avoid… https://t.co/00lei2F4Lt
— DotsamaNFT (@DotsamaNFT_com) August 31, 2023
Moreover, always verify the network you are sending your transactions. If using a hot wallet, ensure you are on the correct network.
9. Don’t Make Yourself A Target!
Resisting the temptation to boast about your crypto investment successes on social media is crucial, as openly bragging about your gains can inadvertently attract potential attackers.
Undoubtedly, maintaining a low profile in the online space is essential to safeguard your Web3 assets. It involves refraining from boasting about your financial achievements or revealing personal information (doxing) on social media platforms. Such actions can make you vulnerable to scammers or hackers seeking to exploit your assets.
Conclusion
Although implementing robust security measures to safeguard your cryptocurrency may seem like a lot of effort, protecting your investment from potential hackers is undeniably crucial.
Remember, the ease of access for you is also the ease of access for attackers.
By adhering to these best practices, you will enhance the security of your crypto wallet and fortify your overall online interactions, as any online transaction can be susceptible to threats.
Moreover, it’s essential to understand that the chances of recovering lost or stolen crypto assets are nearly nonexistent. Therefore, investing in upfront preventative security measures is undoubtedly worthwhile.
As cyber-attacks continuously evolve, so do the methods of protecting yourself. Staying vigilant and monitoring news updates for information on new attacks or threats will enable you to respond swiftly in case your crypto wallet becomes vulnerable. DYOR!!!
– For more cryptocurrency news, check out the Altcoin Buzz YouTube channel.
– Manage Your Crypto Portfolio with Regular Updates and Top Insights for only $15/ month. Join Altcoin Buzz Alpha on Patreon or on Youtube!
Disclaimer
The information discussed by Altcoin Buzz is not financial advice. This is for educational, entertainment, and informational purposes only. Any information or strategies are thoughts and opinions relevant to the accepted levels of risk tolerance of the writer/reviewers and their risk tolerance may be different than yours. We are not responsible for any losses that you may incur as a result of any investments directly or indirectly related to the information provided. Bitcoin and other cryptocurrencies are high-risk investments so please do your due diligence. Copyright Altcoin Buzz Pte Ltd.
The post How to Protect Your Coins From Hacks appeared first on Altcoin Buzz.
