

Getty Images
Phishing mongers have released a torrent of image-based junk emails that embed QR codes into their bodies to successfully bypass security protections and provide a level of customization to more easily fool recipients, researchers said.
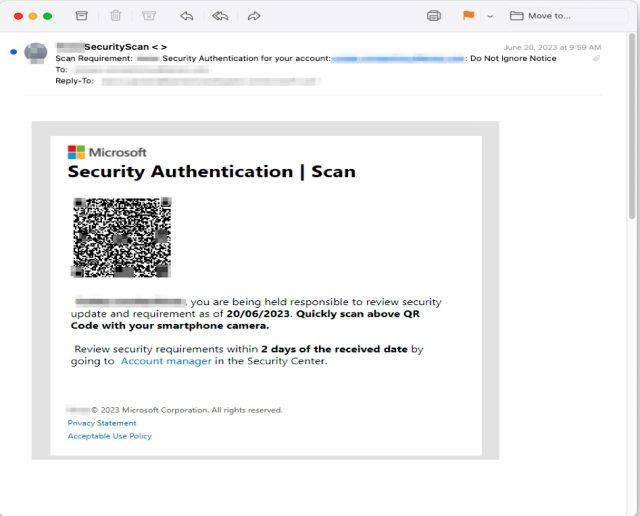
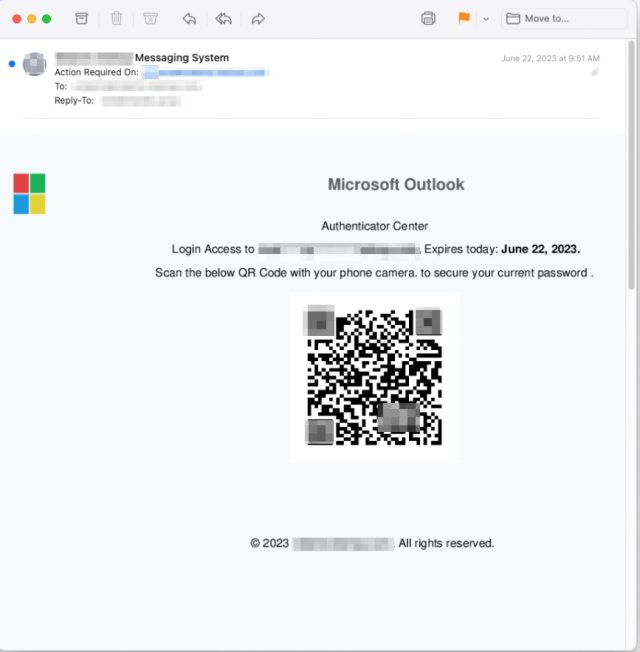
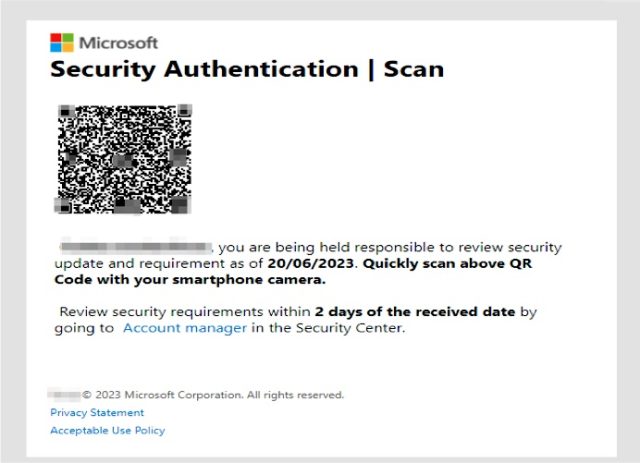
In many cases, the emails come from a compromised email address inside the organization the recipient works in, a tactic that provides a false sense of authenticity, researchers from security firm Inky said. The emails Inky detected instruct the employee to resolve security issues such as a missing two-factor authentication enrollment or to change a password and warn of repercussions that may occur if the recipient fails to follow through. Those who take the bait and click on the QR code are led to a site masquerading as a legitimate one used by the company but it captures passwords and sends them to the attackers.
Inky described the campaign’s approach as “spray and pray” because the threat actors behind it send the emails to as many people as possible to generate results.
There are a few things that make this campaign stand out. First, the emails contain no text. Instead, they have only an attached image file. This allows the emails to escape notice by security protections that analyze the text-based words sent in an email. Some email programs and services, by default, automatically display attached images directly in the body, with some providing no way to suppress them. Recipients then often don’t notice that the image-based email contains no text.
Another distinguishing feature: the images embed a QR code that leads to the credential-harvesting site. This can reduce the time it takes to visit the site and lower the chance the employee will realize something is amiss. The QR codes also cause the loaded website to prefill the recipient’s unique email address in the username field. This adds another false sense of assurance that the email and site are legitimate.
Inky
Inky
In a writeup published Friday, the Inky researchers wrote:
It’s important to note that these three QR Code phishing emails weren’t sent to just a handful of INKY customers. They were part of a “spray and pray” approach. Phishers send their emails to as many people as possible (spray) and then hope (pray) that a strong majority of recipients will fall for the ruse. In this case, multiple industries were attacked. Of the 545 emails noted thus far, intended victims were in the US and Australia. They included nonprofits, multiple wealth management firms, management consultants, a land surveyor, flooring company, and more.
It has long been possible—not to mention a good practice—for privacy-minded people to configure email settings to block the loading of images stored remotely. Scammers and snoops use external images to determine if a message they sent has been opened since the recipient’s device makes a connection to a server hosting the image. Gmail and Thunderbird don’t display attached images in the body, but Inky said other clients or services do. People using such clients or services should turn off this feature if possible.
Unfortunately, it’s more problematic to block images that are embedded into an email. I couldn’t find a setting in Gmail to suppress the loading of embedded images. Thunderbird prevents embedded images from being displayed, but it requires reading the entire message plaintext mode. That, in turn, breaks helpful formatting.
All of this leaves users with the same countermeasures that have been failing them for decades now. They include:
- Seek confirmation that a message is legitimate by checking with the sender through out-of-band means, meaning through a channel other than email
- Take extra care in inspecting the sender’s address to ensure the email comes from where it claims
- Click on the body of an email and see if the text can be copied and pasted. If there are no text-based words, be extra suspicious.
It’s easy for people to dismiss phishing attacks as unsophisticated and perpetuate the myth that only inattentive people fall for them. In fact, studies and anecdotal evidence suggest that phishing is among the most effective and cost-effective means for carrying out network intrusions. With 3.4 billion spam emails sent every day, according to AGG IT Services, and one in four people reporting they have clicked on a phishing email at work, according to Tessian, people underestimate the costs of phishing at their own peril.
